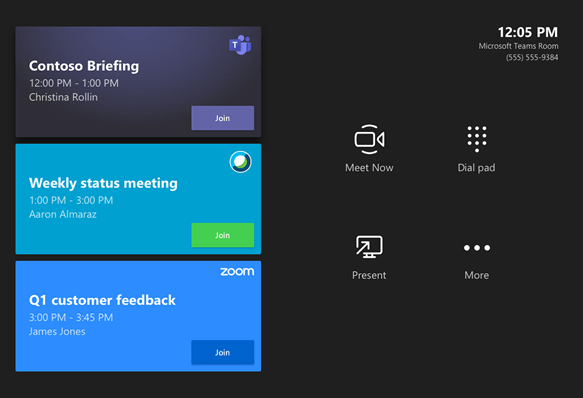
Join WebEx on MTR
The “Join Cisco WebEx meetings from Teams Rooms with direct guest join” was introduced with Microsoft Teams Room version 4.5.35.0, please see the Release Notes.
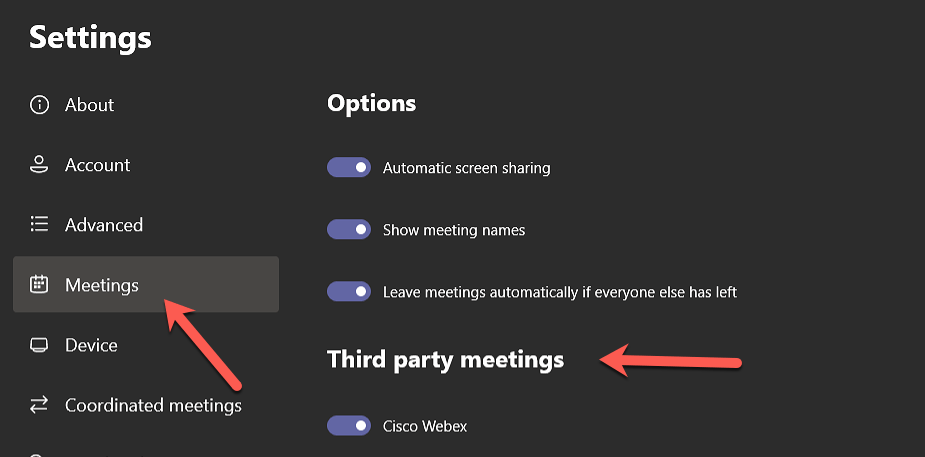
Modify the MTR config
If you use the “Safe Link” AntiSpam/Security Feature in Exchange Online Protection (EOP) or Advanced Threat Protection (ATP) you might want to exclude the URLs for Microsoft Teams, Cisco Webex and Zoom meetings. If you do not exclude the rewrites of these URLs, the Microsoft Teams Room (MTR) is unable to handle the altered URLs and the join will not work.
Guest join is not working
The altered/rewritten URLs looks like this: https://eur03.safelinks.protection.outlook.com/?url=https
You can use the Exchange Admin Center (EAC) to change that behaviour.
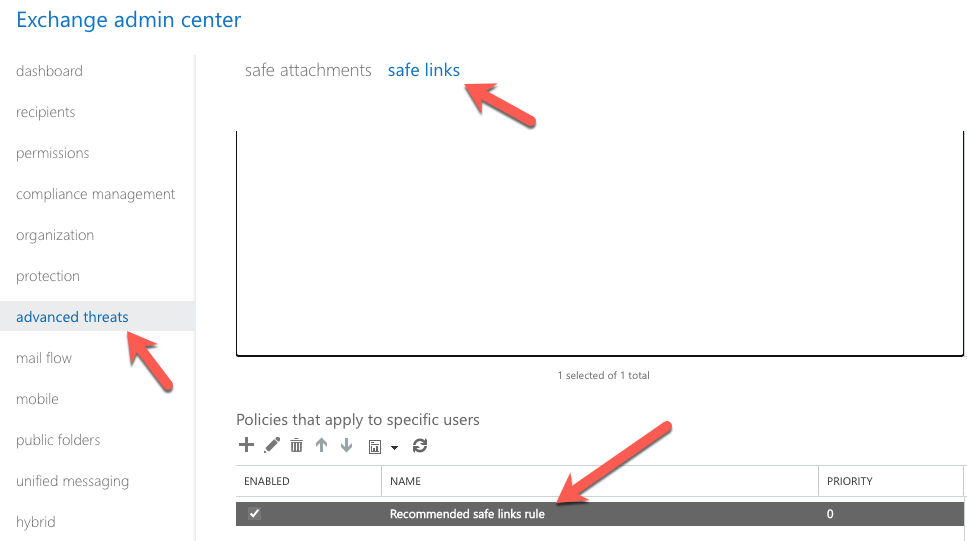
Where to find it
You will find this in “advanced threats/safe links”.
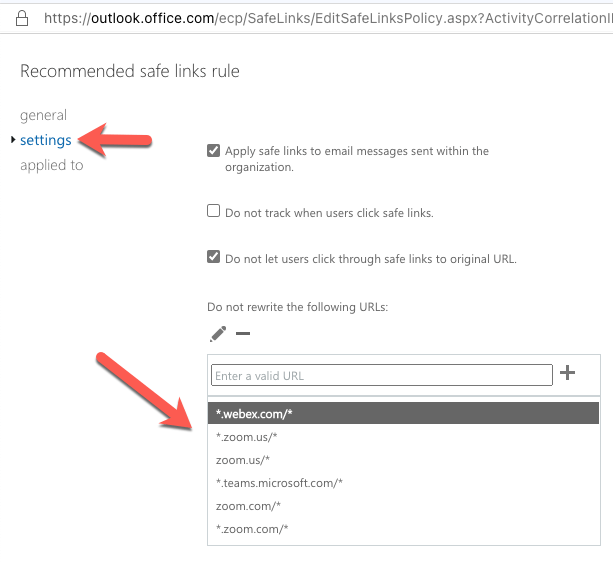
Modify the Policy
I recommend to exclude the following URLs:
'*.webex.com/*'
'*.zoom.us/*'
'zoom.us/*'
'*.teams.microsoft.com/*'
'teams.microsoft.com/*'
'zoom.com/*'
'*.zoom.com/*'
Guest join is working
If you have multiple Rules, you might want to use PowerShell to automate this process!
# Get your active SafeLinks Policy/Policies
Get-SafeLinksPolicy | Where-Object -FilterScript {
$_.IsEnabled -eq $true
} | Select-Object -ExpandProperty Identity
# I use the default policy in this example
$SafeLinksPolicyIdentity = 'Recommended safe links policy'
# A list of URLs to exclude from rewriting
$DoNotRewriteUrls = @(
'*.webex.com/*'
'*.zoom.us/*'
'zoom.us/*'
'*.teams.microsoft.com/*'
'teams.microsoft.com/*'
'zoom.com/*'
'*.zoom.com/*'
)
# I use the default policy in this example
Set-SafeLinksPolicy -Identity $SafeLinksPolicyIdentity -DoNotRewriteUrls $DoNotRewriteUrls
<#
Note:
The WhiteListedUrls and ExcludedUrls parameters are deprecated
Only use the DoNotRewriteUrls parameter
#>
# Remove all URLs from the SafeLinks Policy/Policies
$DoNotRewriteUrls = @()
Set-SafeLinksPolicy -Identity $SafeLinksPolicyIdentity -DoNotRewriteUrls $DoNotRewriteUrls
I also recommend a few more things for the SafeLinks policy/policies:
# Apply my recommended settings to the policy/policies
$paramSetSafeLinksPolicy = @{
Identity = $SafeLinksPolicyIdentity
DoNotTrackUserClicks = $false
DoNotAllowClickThrough = $true
ScanUrls = $true
EnableForInternalSenders = $true
DeliverMessageAfterScan = $true
}
Set-SafeLinksPolicy @paramSetSafeLinksPolicy
<#
Identity = The Identity parameter specifies the Safe Links policy that you want to modify
DoNotTrackUserClicks = Track user clicks related to links in email messages and Microsoft Teams
DoNotAllowClickThrough = Disallow users to click through to the original URL
ScanUrls = Enable real-time scanning of links in email messages
EnableForInternalSenders = The policy is applied to internal and external senders
DeliverMessageAfterScan = Wait until Safe Links scanning is complete before delivering the message
#>
This is fine, no panic:
WARNING: The command completed successfully but no settings of 'Recommended safe links policy' have been modified.
If you let external parties and/or services to invite your Microsoft Teams Room (MTR) directly, you need to tweak the calendar processing for it/them:
# Do this for all your Teams Room Devices that should except external invitations
Set-CalendarProcessing -Identity '<Your Device here>' -ProcessExternalMeetingMessages $true
The code above looks crappy on my Blog, but there is a GIST for all the Code above!