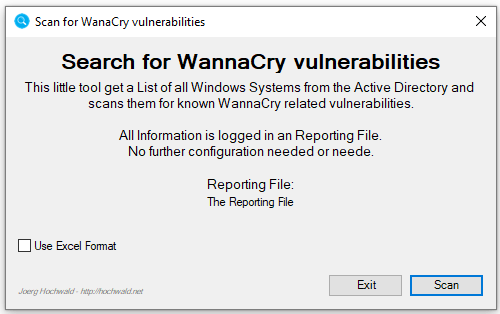
A couple of days ago, I published a free tool to scan your Active Directory for all Windows based Systems and report if the EternalBlue (WannaCry) related Hotfixes are installed.
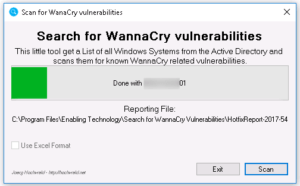
Today, I published a new and extended version of the tool: The scan is much more accurate and it also reports the EternalBlue (WannaCry) related SMBv1 informations. The tool now generates a CSV reporting instead of the simple text based from the old version. That makes it easy to use Excel (or any other tool that can do the Job) to filter and reuse the reporting data.
The tool is available for free (Freeware and Public Domain) on GitHub. The Source is still not published and never will be! There are parts the Enabling Technology Framework included, and this is not open Source. But the basic idea is based on the Gist Files I published here and on GitHub.
Here is a quick overview of the changes:
- Changed the Output from plain ASC Text to CSV
- Use some CIM calls to gather the needed information
- Export to Excel to support native Excel Files instead of CSV Had some issues with that.
- Gather more infos (e.g. the SMBv1 related infos)
- Get all related Hotfixes
- UI improved
- Elevation (Admin) check
- Scan now shows a bit more info while it runs
- Installer is now 64Bit
- Name of the installer is changed
- Default location is changed (for the installer)
- Now all Windows based systems are reported (Even newer Windows 10 based systems
You will find the Executable and an Installer on the GitHub Page for the tool. The old version of both is still available on the GitHub Page.