In our Office Location we have a VDSL100 Business (up to 100 MBit/s downstream with an up to 40 MBit/s upstream) by Deutsche Telekom, with one (1) fixed IPv4 and a big IPv6 network. Before we had a FritzBox attached to the VDSL and used a pfSense behind it. The new setup (due to the issues with double NAT) looks like this: A Draytek Vigor130 as VDSL Modem and an UniFi Security Gateway 3P as Firewall/Router.
We configured the Draytek Vigor130 as a VDSL Modem. That was simple by doing the following in the Web Interface of the Draytek Vigor130, goto Internet Access > General Setup:
 > Internet Access > General Setup
> Internet Access > General Setup
The Tag value is the VLAN that our ISP is using: VLAN 7
You can ignore this here and do that on the UniFi Security Gateway, but I like to do that as soon as possible so I decided to do it on the Modem. We tested both, and both configurations seemed to work just fine.
Goto Internet Access > PPPoE / PPPoA and disable PPPoE/PPPoA Client:
 > Internet Access > PPPoE / PPPoA
> Internet Access > PPPoE / PPPoA
Everything will be greyed out then!
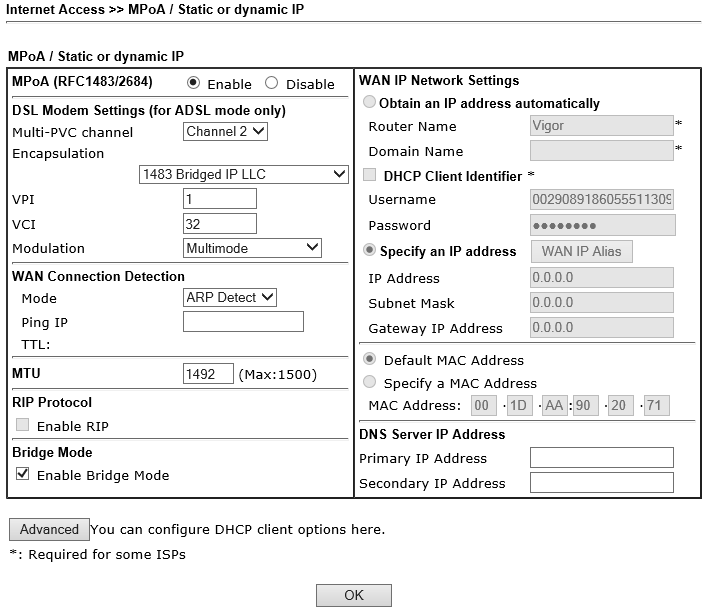
Goto Internet Access > MPoA / Static or dynamic IP and enable MPoA (RFC1483/2684) and Bridge Mode:
 > Internet Access > MPoA / Static or dynamic IP
> Internet Access > MPoA / Static or dynamic IP
Remark: We had to set the MTU to 1492 here, I will write about that a bit later.
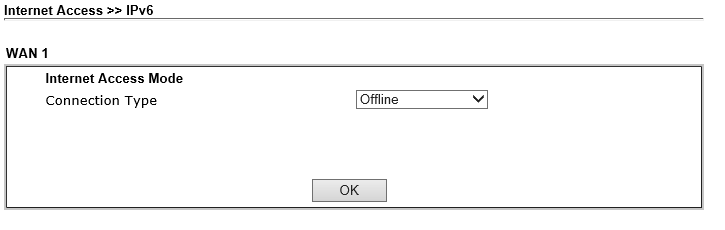
Goto Internet Access > IPv6 and disable it (might be already the case)
 > Internet Access > IPv6
> Internet Access > IPv6
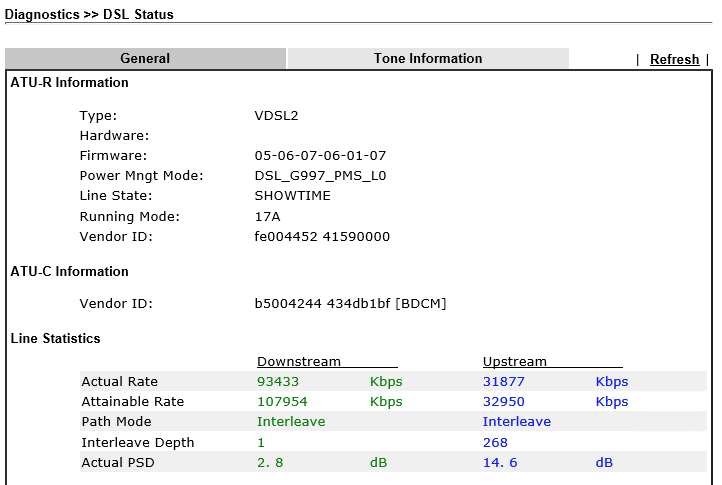
The Draytek Vigor130 reboots and should bring up the connection. Goto Diagnostics > DSL Status and wait until you see SHOWTIME
 > Diagnostics > DSL Status
> Diagnostics > DSL Status
Please note: Online Status > Physical Connection is another way to see if the Draytek Vigor130 is connected.
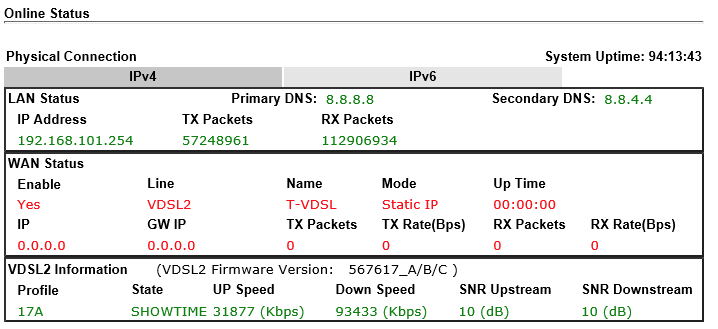 > Online Status > Physical Connection
> Online Status > Physical Connection
However, the WAN Status shows that the Draytek Vigor130 is Offline. That makes sense, cause the Draytek Vigor130 acts as a Modem only now. Nevertheless, the LAN Status and the VDSL2 Information might be still useful for you!
At the moment we use the Draytek Firmware 3.8.4_m7
Now open the UniFi Controller and go to Settings > Networks > WAN
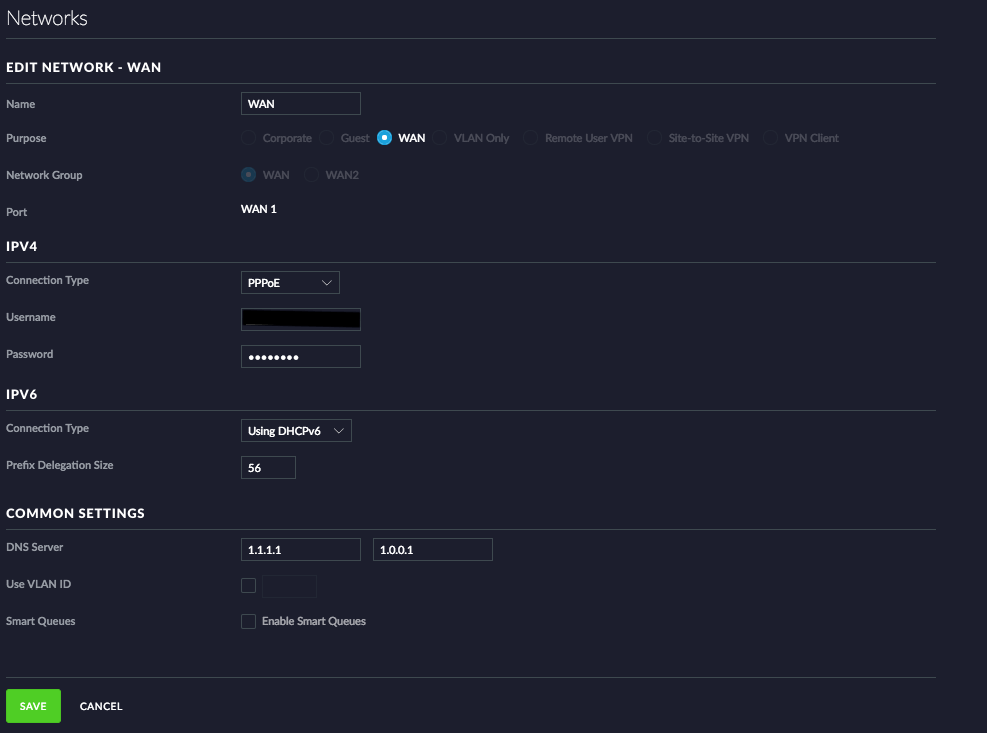 > Settings > Networks > WAN
> Settings > Networks > WAN
In IPV4 select PPPoE
Your Username (If you have a regular Telekom VSDL contract) is in the following format: [email protected] (dummy example [email protected])
In IPV6 select Using DHCPv6
We have to use a Prefix Delegation Size of 56 (Our ISP provides an /64 routing network and an /56 network for us).
In the COMMON SETTINGS you can provide the external DNS Servers to use, most people I know use the Google DNS Servers (8.8.8.8 and 8.8.4.4)! I prefer to use the CloudFlare DNS Servers (1.1.1.1 and 1.0.0.1) instead. You might also want to use your ISP’s DNS Server.
If you do not Tag the PPoE VLAN on the Draytek (as we do), you have to select Use VLAN ID and put it in here!
About Smart Queues: I would love to use them, but we found out, that this causes a lot of issues! So we decided to leave them off for now!
After the provisioning of the Controller should show something like this:
 More Details
More Details
 Controller Status
Controller Status
 Details
Details
You should be able to access the Internet from within your local Network (LAN)! And you might want to run some Speed Tests to check if everything works as it should!
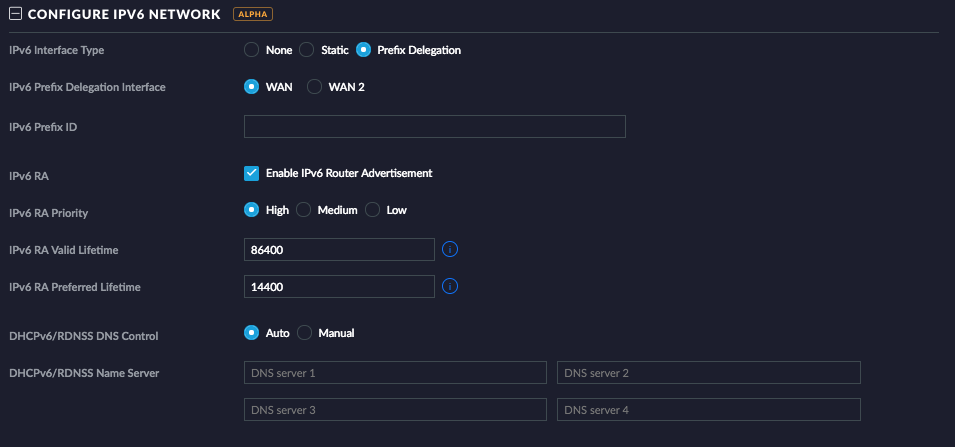
Now you might want to configure your IPv6 networking! In the UniFi Controller and go to Settings > Networks > YOURLAN > EDIT NETWORK
Try Prefix Delegation here, and the UniFi Security Gateway will provide something out of the big range for you.
 IPv6 Prefix Delegation
IPv6 Prefix Delegation
In our case that doesn’t work! I tried everything but the internal interface never offered an IPv6 lease, and never advertised itself as a Router (IPv6 RA)!!!
I think, that this is caused by the two networks that our ISP routes to us. The UniFi Security Gateway will get an Address on the WAN Interface out of the /64 routing network. And it looks like the UniFi Security Gateway is unable to handle the separated /56 and slice it to smaller chunks.
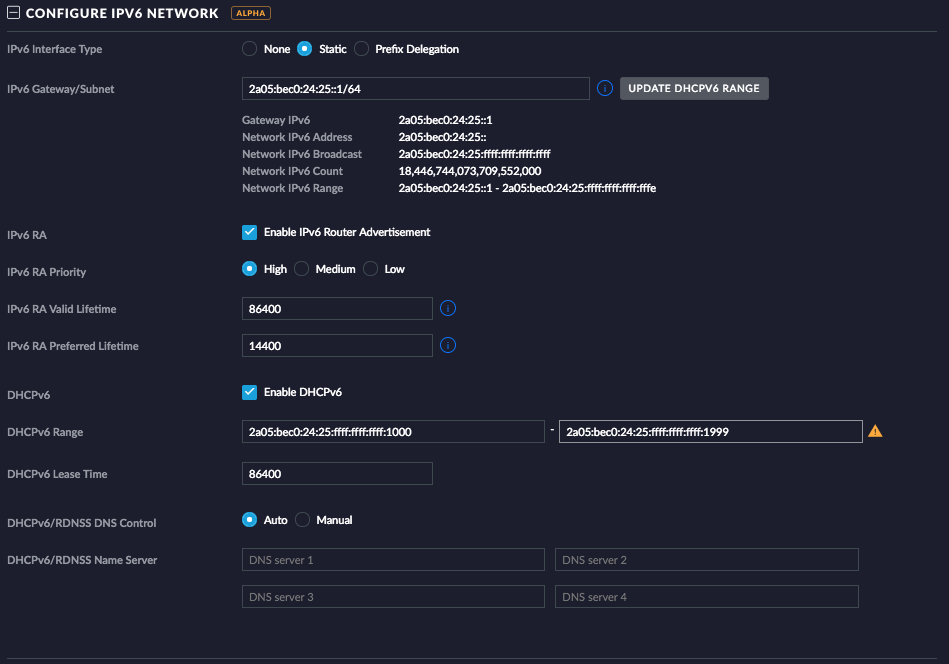
So I decided to split our /56 IPv6 network into /64 chunks. I know that many other vendors didn’t like IPv6 networks bigger than /64 as well!
Here is an example:
 IPv6 Example
IPv6 Example
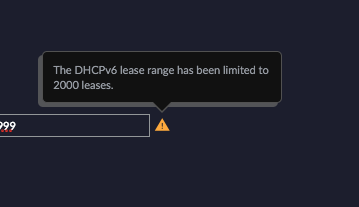
Please note: The IPv6 DHCP range is limited to 2000 entries:
 IPv6 Range
IPv6 Range
And now all your clients can access the Internet via IPv4 and IPv6.
But now I found the following issue: The CPU load on the UniFi Security Gateway was constantly over 60%, while the connection was idle. All caused by the dhcpv6-pd-respo process.
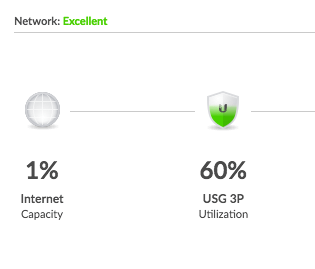 Load was high
Load was high
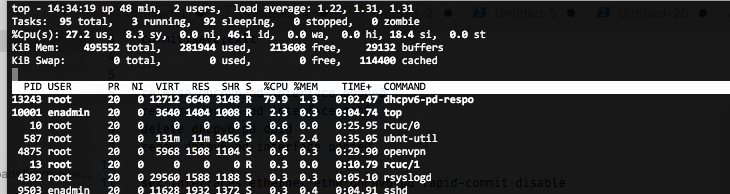 Info with TOP
Info with TOP
With the help of the community Forum and a lot of Web Searches, I figured out how to solve that.
Open a SSH Session to you UniFi Security Gateway and do the following:
configure
set interfaces ethernet eth0 dhcpv6-pd prefix-only
set interfaces ethernet eth0 pppoe 0 dhcpv6-pd prefix-only
commit;save;exit
Save this snippet somewhere! It will be gone when the UniFi Security Gateway provisions again. However, you will see that immediately (Load might go up very quick).
Another issue that we found: Sometimes the UniFi Security Gateway gets an external IPv6 address, but it stops to advertise them internally! We have some servers that have fixed IPv6 addresses (outside of the DHCP) range, and they will not be able to access the Internet then.
So I did the following (SSH to you UniFi Security Gateway again):
release dhcpv6-pd interface pppoe0
release dhcpv6-pd interface eth0
delete dhcpv6-pd duid
renew dhcpv6-pd interface pppoe0
We also had this issue twice in one of our home-office locations where we used prefix delegation. It just stopped working after a few weeks. The Workaround above solved that issue.
Last but not least: As soon as you configure your UniFi Security Gateway as the Internet Gateway, you will not be able to access your Draytek Vigor130 anymore!
Under normal circumstances, this is OK! But if you need to update the Firmware and/or want to check the DSL connection, here is a workaround for you:
configure
set interfaces ethernet eth0 address 192.168.101.1/24
set service nat rule 5001 description 'masquerade for WAN'
set service nat rule 5001 destination address 192.168.101.0/24
set service nat rule 5001 outbound-interface eth0
set service nat rule 5001 type masquerade
set service nat rule 5001 protocol all
set interfaces ethernet eth0 address 192.168.101.1/24
commit;save;exit
What this will do: It assign a private IPv4 address out if the range where your Draytek Vigor130 is. In the example above, the Draytek Vigor130 has 192.168.101.254 and the UniFi Security Gateway has 192.168.101.1. You can use whatever you like, just adopt the example above. The example also creates a NAT Rule, that is needed if you want to access the Webinterface from your clients (from your LAN).
As mentioned above: After provisioning, this might be gone.
Nevertheless, in our office location, the UniFi Security Gateway was never really stable! Sometimes a big download from one client makes the complete gateway unstable, and it dropped all connections. Because we were never able to solve that, we decided to remove the UniFi Security Gateway 3P and replace it with another solution (from another vendor).
Why did we do that? When we used the Draytek Vigor130 as a router (instead of just a modem) everything worked fine. As soon as we switched back to the UniFi Security Gateway as a router/gateway, it was unstable again. And we also tried it with an AVM Fritzbox 7590 (with and without the Draytek Vigor130 as Modem in-front) and it just worked smooth and very stable.
The new solution (Cisco) works just fine with the Draytek Vigor130 as a VDSL Modem. Stable and rock-solid!!!