I’m a big fan of HAProxy and I try to use it whenever possible. It’s reliable and flexible Open Source Load Balancer for TCP and HTTP. The only thing you might miss: A nice Web GUI! I also like the Open Source Firewall pfSense a lot! Best of all: There is a HAProxy package for pfSense that provide a nice Web UI.
A friend told me:
I want to protect a backend Server with basic authentication, and this is not working with the pfSense package of HAProxy.
He was wrong: It is possible, but the process is not directly implemented within the UI.
Based on the HAProxy documentation, create a UserList. You can use DES, MD5, SHA-256, and SHA-512 encrypted passwords. If you really know what you are doing: You can use plain text passwords here as well, but they are stored as plain text within the config files and can not recommend to do so!
Sample of a userlist with the name UserGroup
userlist UserGroup
user User1 password SECRET
user User2 password SECRET
Same as above with plain text passwords:
userlist UserGroup
user User1 insecure-password YourInsecurePasswordStringHere
user User2 insecure-password YourInsecurePasswordStringHere
Again: I highly recommend to use encrypted passwords! My example will use SHA-512 encrypted passwords.
Paste the snippet above to the custom options on the HAProxy settings:
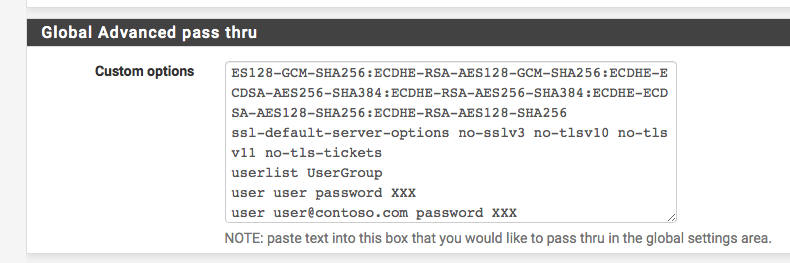 Custom options on the HAProxy settings
Custom options on the HAProxy settings
Please note the following: Always put the userlist to the end of you custom options!
 Reminder: Put this to the end!
Reminder: Put this to the end!
Now modify your Access control lists and actions. You can do this for a Frontend and/or Backend: In my Example I use a “Access Control list” as “Custom acl” with the name “BackendAccess” and the Value “http_auth(UserGroup)” We create a “Action” as “http-request auth” with the “realm:” vale of “realm UserGroup unless BackendAccess”. Please leave the “Condition acl names” empty.
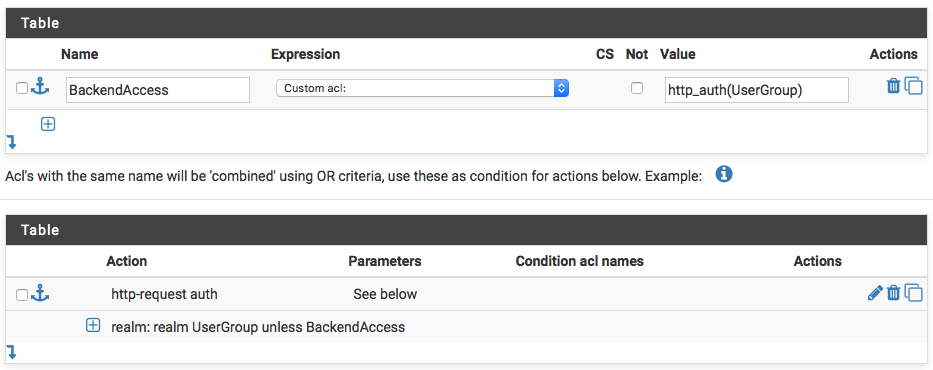 Access control lists and actions
Access control lists and actions
You might ask yourself: how should I create the encrypted passwords? I use Python to do this:
python -c 'import crypt,getpass; print(crypt.crypt(getpass.getpass(), crypt.mksalt(crypt.METHOD_SHA512)))'
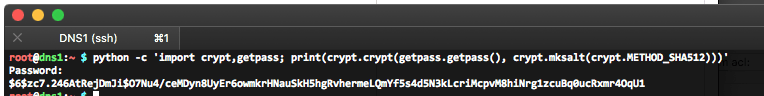 Use Python to create encrypted password
Use Python to create encrypted password
A more automated way to do it:
python -c 'import crypt; print(crypt.crypt("TheSuperSecretPasswordHere", crypt.mksalt(crypt.METHOD_SHA512)))'
 Use Python to create encrypted password
Use Python to create encrypted password
On Debian you can use the mkpasswd command (This is, why-ever, part of the whois package):
printf "TheSuperSecretPasswordHere" | mkpasswd --stdin --method=sha-512
On the Mac you can use HomeBrew to install Python 3:
/usr/local/bin/python3 -c 'import crypt,getpass; print(crypt.crypt(getpass.getpass(), crypt.mksalt(crypt.METHOD_SHA512)))'
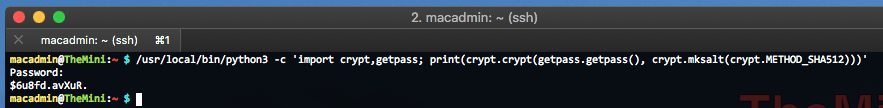 Use Python on macOS to create encrypted password
Use Python on macOS to create encrypted password
You might need a more complex solution, with different access levels or access based on groups. You can do this with HAProxy!!!
Just edit your UserList like this:
userlist UserGroup
group is-user
group is-admin
user User1 password SECRET groups is-user
user User2 password SECRET groups is-admin
All users can access the backend protected with the example above! If you want another Backend, lets say just for admins, use the following rule: Create a “Custom acl” in “Access Control list” with the name “AdminAccess” and the Value “http_auth_group(basic-auth-list) is-admin” Now create a “Action” as “http-request auth” with the “realm:” vale of “realm Admin unless AdminAccess”.
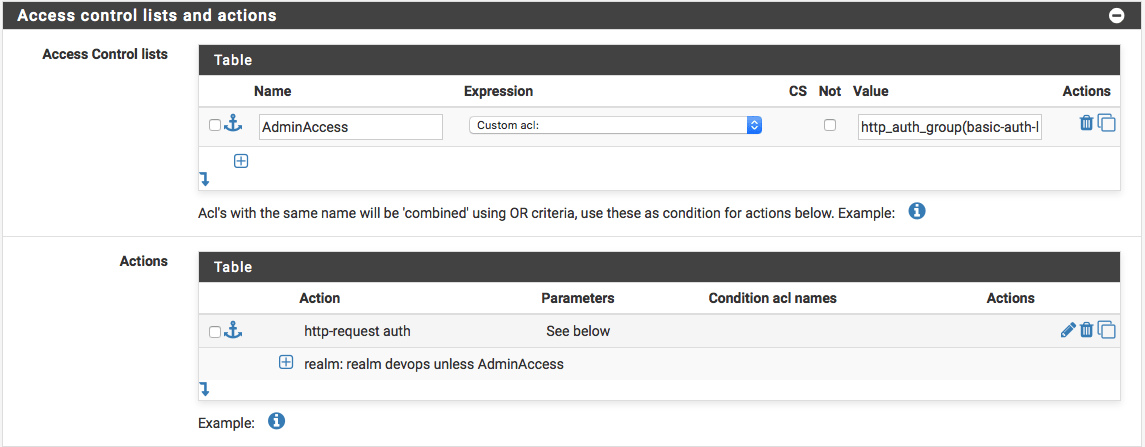 Another Example
Another Example
