In the vast digital landscape, where information flows freely and creativity knows no bounds, there exists a seemingly innocuous tool that has recently taken a sinister turn. Microsoft OneNote, a popular note-taking application, has become an unexpected conduit for cyber attacks. In this blog post, we delve into the shadowy world of OneNote abuse, where seemingly harmless notes harbor hidden dangers.
The Rise of Malicious OneNote Files
Traditionally, attackers relied on macros within Office applications to deliver their payloads. However, with macros disabled by default, cybercriminals have adapted. Enter OneNote—the unsuspecting accomplice in this new wave of attacks. The Unit 42 Incident Response team analyzed over 6.000 malicious samples and uncovered an alarming trend: OneNote files are abused as carriers of malevolence!
The Art of Deception
Malicious OneNote files masquerade as legitimate notes, luring victims with enticing images and buttons. These seemingly harmless elements hide a darker purpose. When clicked, they trigger the execution of hidden payloads, leading to a variety of harmful outcomes.
The attackers’ creativity knows no bounds; they exploit OneNote’s embedding capabilities to their advantage.
Some examples from the Unit 42 Incident Response team: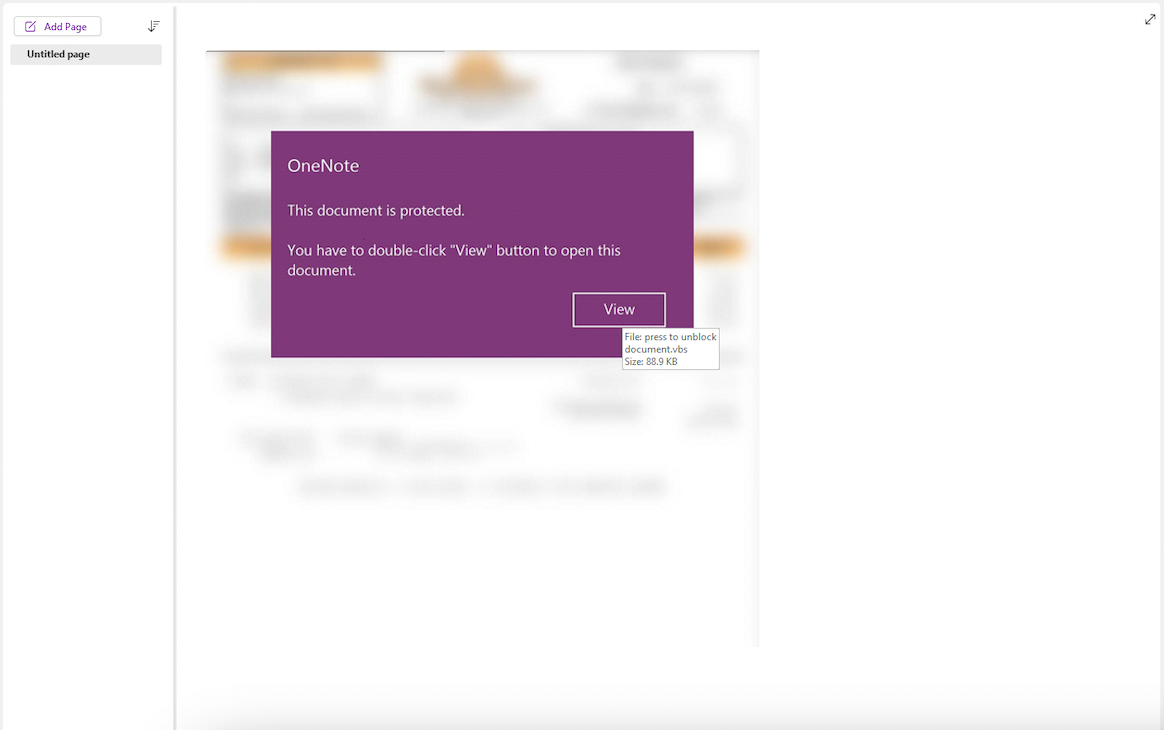
Figure 1
OneNote sample with embedded malicious VBS.
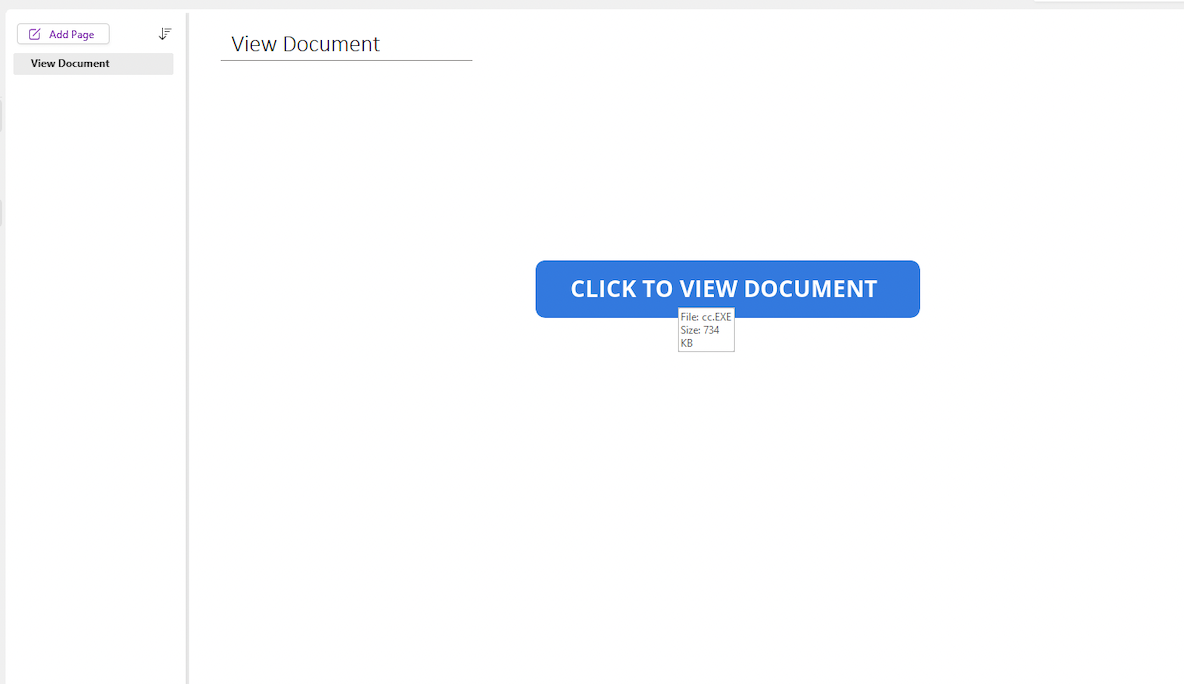
Figure 2
OneNote sample with embedded malicious EXE file.
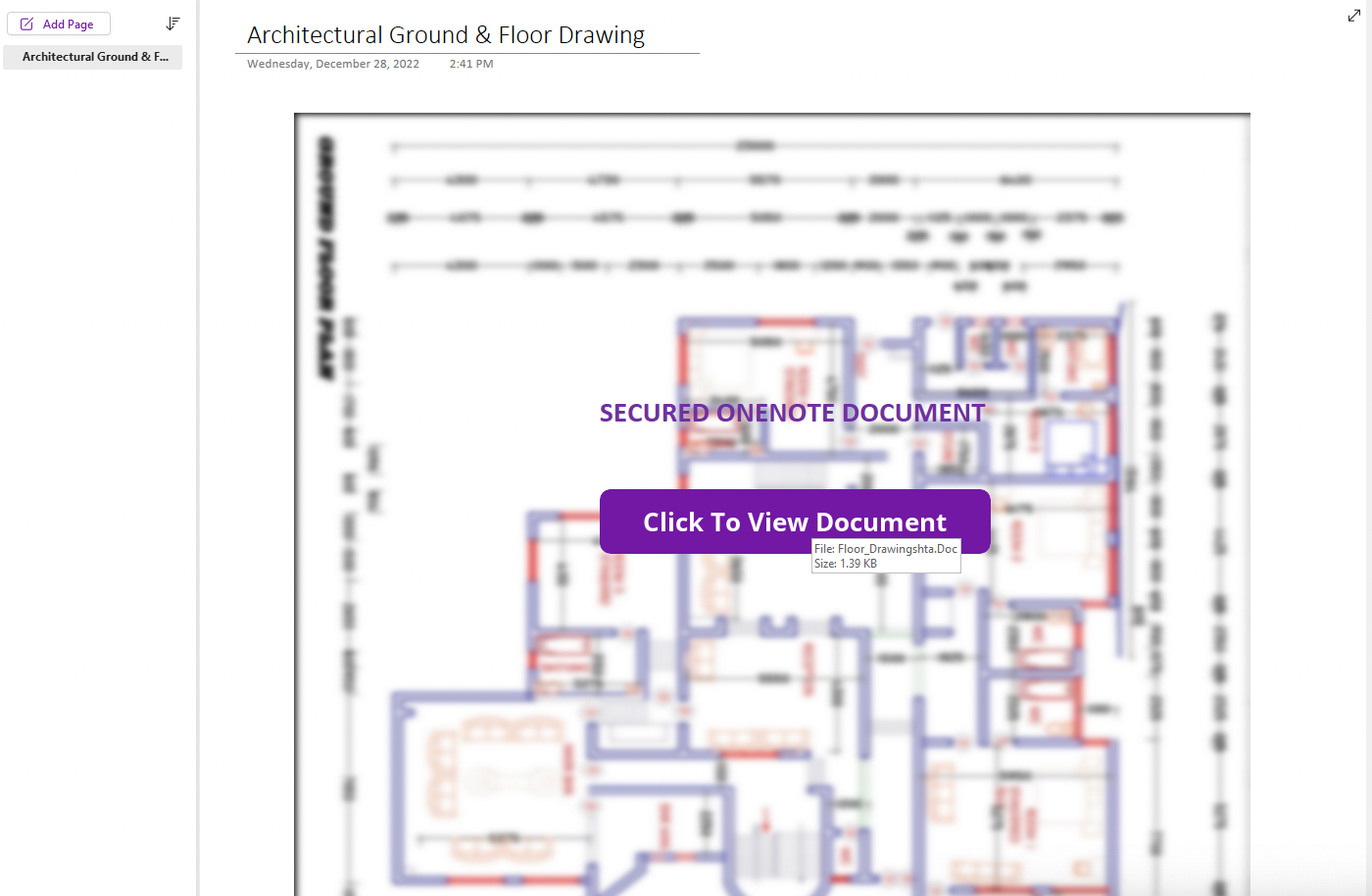
Figure 3
OneNote sample with embedded malicious Office 97-2003 file.
Credit for all the figures above: Unit 42 Incident Response team
The Anatomy of a Malicious OneNote File
- The Tempting Images
Almost all malicious OneNote samples contain at least one image—a visual bait to entice users. These images often resemble innocent buttons, inviting interaction. Hovering over them reveals suspicious file names and extensions, but curiosity often prevails. When clicked, the embedded payloads spring into action, compromising the victim’s system. - Payload Types and Sizes
Attackers favor smaller payloads—JavaScript snippets, for instance—for ease of delivery. These smaller files raise less suspicion when attached to emails. However, larger binary payloads, such as EXE and Office 97-2003 files, pack more capability. The distribution of payload types and their sizes reveals the attackers’ strategic choices. - The Hidden Intent
An in-depth analysis of an embedded EXE payload reveals the malicious intent. Shellcode designed to establish a network socket hints at a reverse TCP shell connecting back to the attacker’s machine. The victim unwittingly becomes a pawn in the cyber chessboard.
Protecting Yourself
- User Vigilance:
Encourage users to exercise caution when opening OneNote files from untrusted sources. Hover over buttons and images to reveal suspicious file names and extensions. - Organizational Measures:
- Consider blocking embedded payloads with dangerous extensions within OneNote files.
- Educate employees about the risks associated with OneNote abuse.
- Security Awareness:
Stay curious but stay safe. As we navigate the digital realm, let’s remain vigilant against seemingly harmless notes harboring hidden threats.
The next time you encounter an alluring OneNote note, remember: Beneath its innocent facade there might be a potential threat.
OneNote, the home of ideas and creativity, now may harbors a darker secret.
